When working with a colleague on a sample SOA 12c project recently I noticed a change in 12c that I had not seen mentioned anywhere yet. In the sample project we were integrating with the Atlassian OnDemand service in order to provision users for Confluence and JIRA. The integration is performed using a SOAP service over SSL. In this situation, like at many of our customers, we needed to import additional trusted certificates into the trust store in order to make the service call over SSL. At many of our customers this is an internal Root CA they use to sign their own certificates for internal use.
When looking at the default settings of the IntegratedServer in JDeveloper 12c we can now see below that it is configured by default to use the OPSS Keystore Service and not a JKS Trust Store.

You can see above that instead of a filesystem URI to a JKS file you now see a kss:// URI. This URI shows that we are using the trust store called “trust” in the system strip of the Keystore Service.
The OPSS Keystore Service is meant to provide a single location for Keystores and Trust stores for all applications running within the Weblogic domain. The only pre-requisite for using the service is that the JRF templates have been applied to your domain, which should be the case for any SOA 12c domain.
Using this service you can now manage all of your certificates through Fusion Middleware Control and WLST. You can navigate to the Security -> Keystore menu under your domain in FMW Control as shown below.

Once on the Keystore page you can select the keystore called trust under the system stripe and select manage.
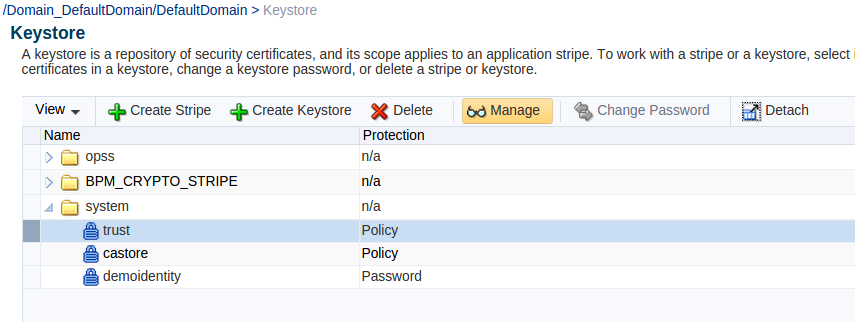
On the Manage Certificates page you can now see a list of all certificates in the keystore. From here you have several operations you can perform such as:
- Generate a Keypair
- Generate a CSR for a Keypair
- Import Certificate
- Import Trusted Certificate
- Export Certificates
- Delete Certificates
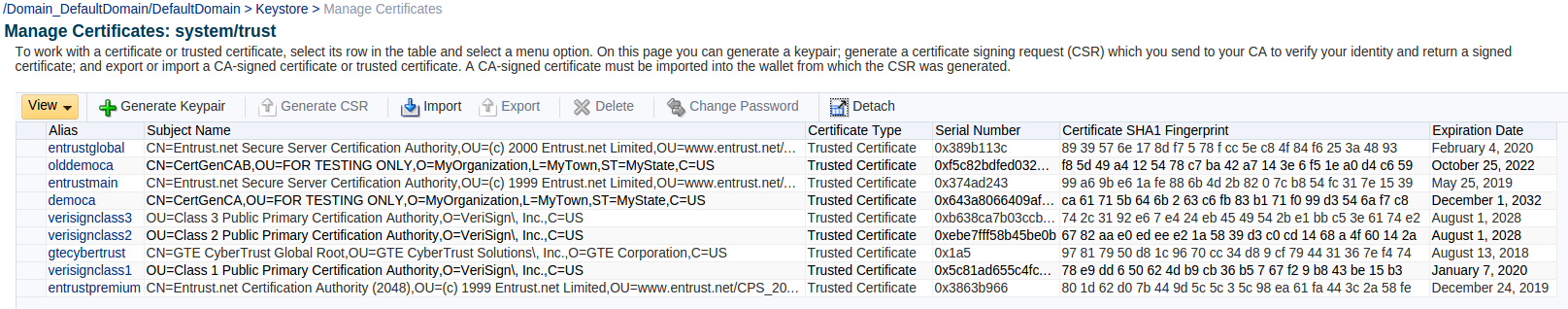
In this case we needed to import several Trusted Certificates so we can simply select the Import button.
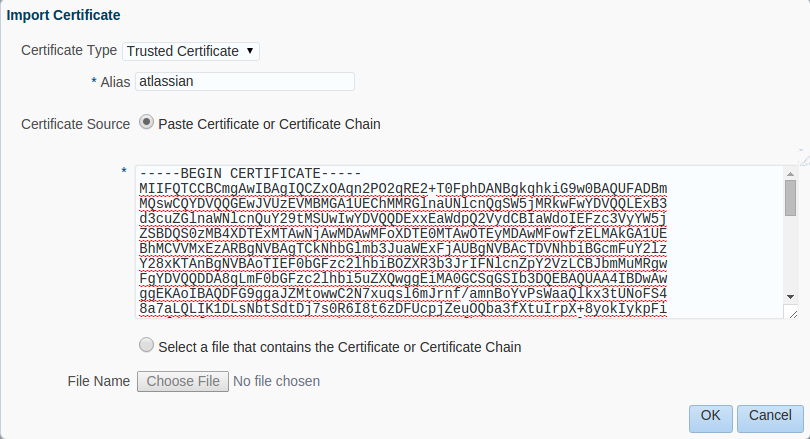
Now we select Trusted Certificate as the type and provide an alias for the certificate.
We can then either paste in the PEM formatted certificate or select it as a file to upload.
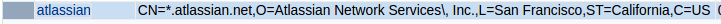
Once imported you should see confirmation that the certificate was imported successfully and you should see the new certificate listed in the table.
‘
Once we imported the required certificates we still needed to restart the integrated server before the service invocation began working.
The OPSS Keystore Service now provides one single point of access for administrators and developers to manage all of the keystores required by each application. This provides administrators a much more user friendly way to generate, sign, and manage their certificates but still allows these actions to be automated through WLST as well.

