HashiCorp Vault is a great place to store your secrets, but how does one quickly and easily integrate from Mule 4? Thankfully, AVIO has a Vault Connector and Vault Properties Provider. And lucky for you, both are open-source and easy to add to your project.
Which One Should You Use?
If you only need to retrieve values from Vault and they aren’t expected to change frequently, use the properties provider. It is best to use the properties provider for database connection details as well as other connectors that require secret information at startup time.
If you need to write secrets, handle data encryption, or retrieve secrets that change often, or are used mid-flow, use the Vault Connector. Secrets can be accessed in real-time via the connector.
Vault Properties Provider
Use the Vault Properties Provider to retrieve values from Vault. Reference values from Vault using this format:
${vault::<secret_engine_path>/<secret_path>.<field_name>}
Properties are loaded from Vault when the application is started, so the application must be restarted to retrieve new values after they are updated in Vault.
For example, one could use properties from Vault to set values in a database connection.
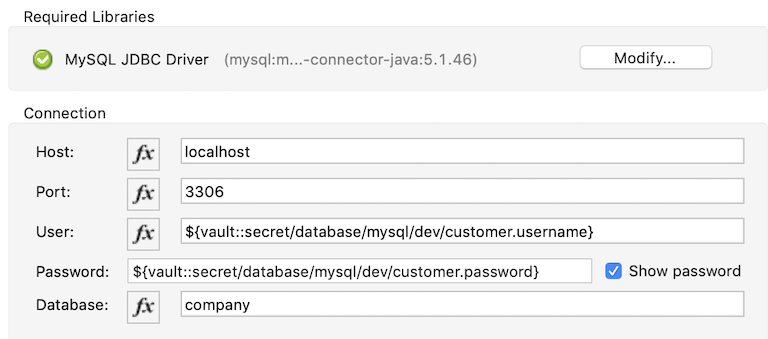
Vault Connector
Use the Vault Connector to read or write secrets at runtime. The connector also has the ability to use the transit secrets engine to encrypt, decrypt, and re-encrypt data.
Set up a Vault connection, then drop a Get Secret component into a flow, specify the secret path, and it’s ready to go.

Authenticating With Vault
Both of the connectors currently enable five types of authentication with Vault.
- Basic Token Authentication
- TLS Authentication
- AWS IAM Authentication
- AWS EC2 Instance Metadata Authentication
- AWS EC2 Identity Document Authentication
Where to Get It
Find the code and installation instructions on GitHub:
- Vault Connector: https://github.com/avioconsulting/mule-vault-connector
- Vault Properties Provider: https://github.com/avioconsulting/mule-vault-properties-provider
Installing the Connectors
Publishing to a private exchange
To publish to a private exchange, some updates are necessary to the projects’ pom.xml files and your Maven settings.xml file.
In the pom.xml files, update the groupId to the Organization ID used by your organization on the Anypoint platform.
In addition, update the url in the distributionManagement section of the pom to the following, replacing ${orgId} with your Organization ID:
https://maven.anypoint.mulesoft.com/api/v1/organizations/${orgID}/maven
Add a server for the exchange repository in your Maven settings.xml file with exchange-repository as the id element and specify the username and password used for Anypoint Exchange.
Installing Into Local Maven Repository
If you would like to install the connectors locally for testing before publishing to exchange, execute mvn install, then manually add the dependency to your project’s pom.xml.
For the Vault Connector, it would look like this:
<dependency>
<groupId>${orgId}</groupId>
<artifactId>vault-connector</artifactId>
<version>0.1.1</version>
<classifier>mule-plugin</classifier>
</dependency>
For the Vault Properties Provider, it would look like this:
<dependency>
<groupId>${orgId}</groupId>
<artifactId>mule-vault-properties-providers-module</artifactId>
<version>0.1.1</version>
<classifier>mule-plugin</classifier>
</dependency>
Now you have a great place to store your secrets and with the help of AVIO’s Vault Connector and Vault Properties Provider, you are all set to quickly integrate HasiCorp Vault from Mule 4!
{{cta(‘899d0e81-5669-4563-88fd-277bf0ac08ec’,’justifycenter’)}}

